Kerberos
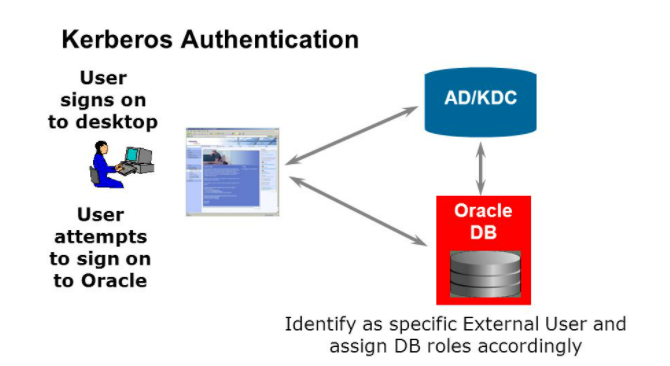
Kerberos is a trusted third-party authentication system. It relies on shared secrets and presumes that the third party is secure. You can configure Oracle Database to use Kerberos authentication. below a kerberos authentication with AD user is specifying
Scenario OS Version RHEL 8, DB Version 19.3.0.0 SE, DBNAME – orcl
Install the kerberos on Database server
yum install krb5-workstation krb5-libs
Required files for kerberos configuration on server
SQLNET.ORA – file where we mention the configuration details
SQLNET.AUTHENTICATION_SERVICES= (BEQ,KERBEROS5PRE,KERBEROS5) SQLNET.FALLBACK_AUTHENTICATION = TRUE SQLNET.KERBEROS5_CC_NAME = /tmp/krb5.cc SQLNET.KERBEROS5_CONF = /etc/krb5.conf SQLNET.KERBEROS5_CONF_MIT = TRUE SQLNET.AUTHENTICATION_KERBEROS5_SERVICE = oracle SQLNET.KERBEROS5_KEYTAB = /u01/app/oracle/product/19.0.0/dbhome_1/network/admin/orcldev01.keytab NAMES.DIRECTORY_PATH= (TNSNAMES, ONAMES, EZCONNECT)
Key tab file, the file that is generated from Domain controller, this file need to be provided by the windows system admin for dba to configure kerberos
orcldev01.keytab - file copy to location specified on sqlnet.ora oklist -k /u01/app/oracle/product/19.0.0/dbhome_1/network/admin/orcldev01.keytab Kerberos Utilities for Linux: Version 19.0.0.0.0 - Production on 03-MAR-2021 16:25:52 Copyright (c) 1996, 2019 Oracle. All rights reserved. Configuration file : /etc/krb5.conf. Keytab name: FILE:/u01/app/oracle/product/19.0.0/dbhome_1/network/admin/orcldev01.keytab KVNO Principal ---- ------------------------------------------------------------ 3 oracle/orcldev01.mithun.local@mithun.LOCAL 3 oracle/orcldev01.mithun.local@mithun.LOCAL 3 oracle/orcldev01.mithun.local@mithun.LOCAL 3 oracle/orcldev01.mithun.local@mithun.LOCAL 3 oracle/orcldev01.mithun.local@mithun.LOCAL File permission -rw-r--r-- 1 oracle oinstall 422 Mar 18 21:04 /u01/app/oracle/product/19.0.0/dbhome_1/network/admin/orcldev01.keytab
Kerbeross Config file – File on server that having the configuration details of the Domain controller
-rw-r--r-- 1 root root 811 Mar 03 10:38 /etc/krb5.conf
vi /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = MITHUN.LOCAL
dns_lookup_realm = true
dns_lookup_kdc = true
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = yes
[realms]
MITHUN.LOCAL = {
kdc = mithun.local:88
admin_server = mithun.local:749
default_domain = MITHUN.LOCAL
}
[domain_realm]
.mithun.local = MITHUN.LOCAL
mithun.local = MITHUN.LOCAL
On database
Set the Initialization Parameters As Kerberos user names can be long, and Oracle user names are limited to 30 characters, Oracle recommends that you set the value of OS_AUTHENT_PREFIX to null in the initialization parameter file.
alter system set OS_AUTHENT_PREFIX=”” scope=both;
Setting this parameter to null overrides the default value of OPS$.
create Database user
If the user’s Kerberos principal name is longer than 30 characters, and up to 1024 characters, then create the user as follows:
SQL> CREATE USER db_user_name IDENTIFIED EXTERNALLY AS 'kerberos_principal_name'
create user mithun identified externally as “mithun.local”
grant connect, resource to mithun
okinit mithun
oklist
now u will be able to access the database
sqlplus /@orcl